A) Cisco Umbrella
B) Cisco Firepower
C) Cisco Identity Services Engine
D) Cisco Advanced Malware Protection
F) A) and C)
Correct Answer

verified
D
Correct Answer
verified
Multiple Choice
Which detail is included in a routing table?
A) broadcast address
B) TCP or UDP port number
C) IP protocol
D) destination next hop or outgoing interface
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 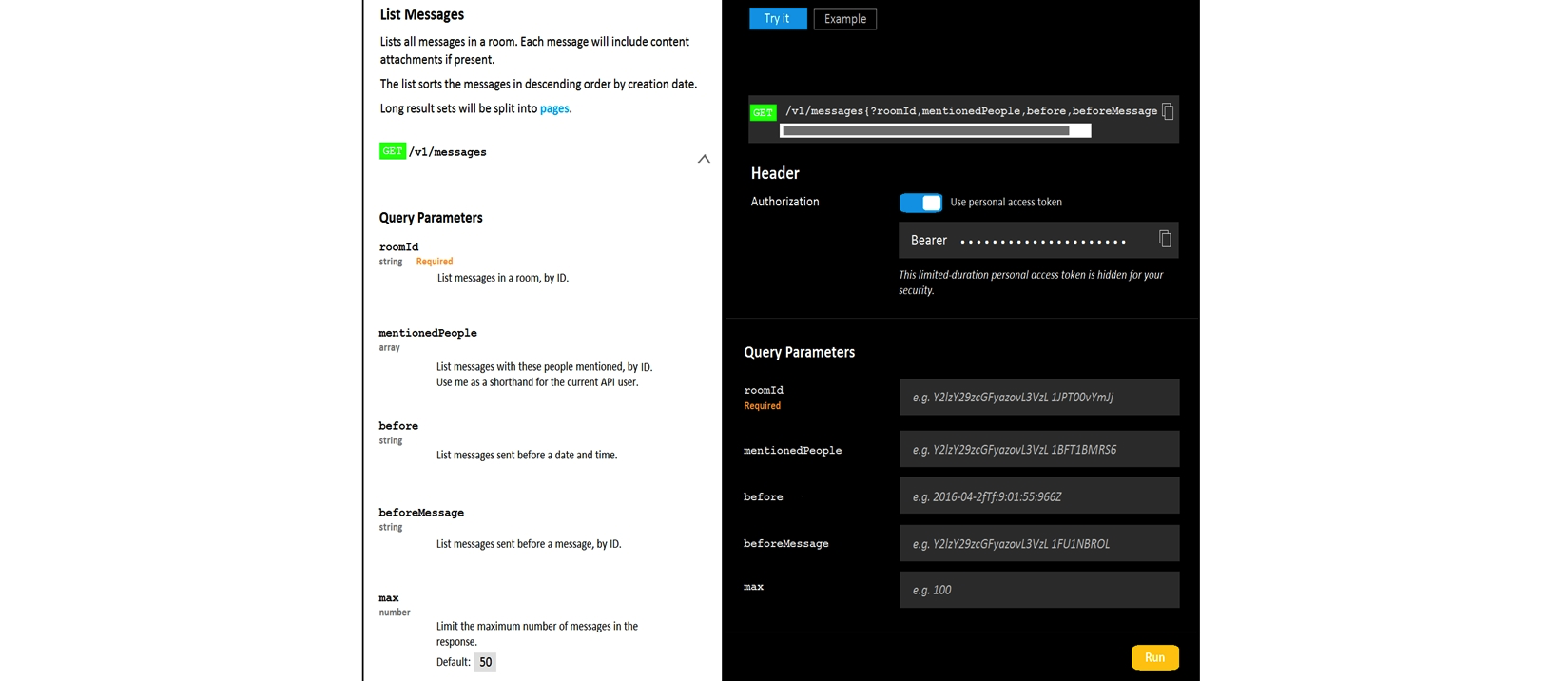
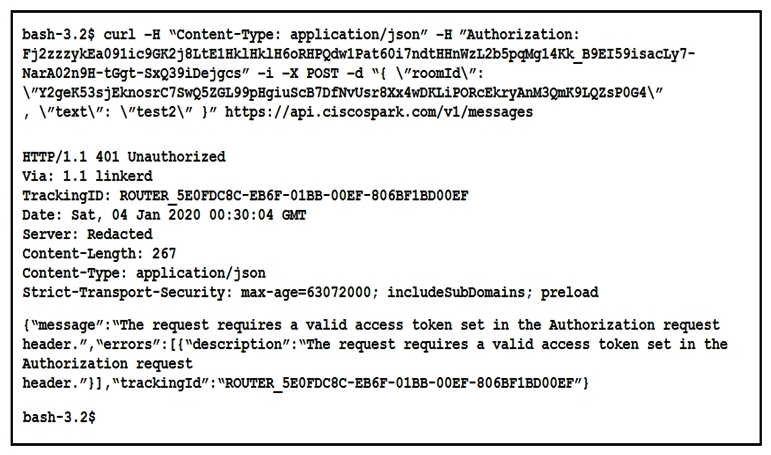 A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem?
A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem?
A) The authorization header is missing or incomplete.
B) The request body is missing or incomplete.
C) The API token specified is expired.
D) The user is not allowed to post messages from their account.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When using the Bash shell, how is the output of the devnet command saved to a file named "output.txt"?
A) devnet > output.txt
B) devnet | output.txt
C) devnet < output.txt
D) devnet & output.txt
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 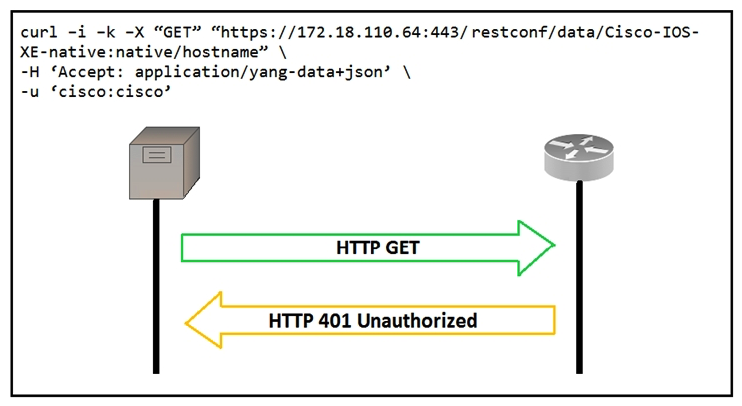 An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue?
An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue?
A) Remove the -H 'Accept: application/yang-data+json' HTTP header because it is not required. Remove the -H 'Accept: application/yang-data+json' HTTP header because it is not required.
B) Use -u cisco:cisco instead of -u 'cisco:cisco' Use -u cisco:cisco instead of -u 'cisco:cisco'
C) Change the request method from -X "GET" to -X "POST" Change the request method from -X "GET" to -X "POST"
D) Add Content-Type HTTP header with ' application/yang-data+json ' using -H 'Content-Type: application/yang-data+json' Add Content-Type HTTP header with ' application/yang-data+json ' using -H 'Content-Type: application/yang-data+json'
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the purpose of a MAC address?
A) to uniquely identify a switch in a LAN
B) to uniquely identify a router in a LAN
C) to uniquely identify a network interface in a LAN
D) to uniquely identify a device on the Internet
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which description of a default gateway is true?
A) It is a security feature that denies certain traffic.
B) It is a device that receives IP packets that have no explicit next-hop in the routing table.
C) It is a feature that translates between public and private addresses.
D) It is a device that receives Layer 2 frames with an unknown destination address.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A function my_func() returns True when it executes normally. Which Python snippet tests ?
A) ![]()
B) ![]()
C) ![]()
D) ![]()
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is a benefit of organizing code into modules?
A) enables the code to be broken down into layers
B) improves collaboration of the development team
C) makes it easier to deal with large and complex systems
D) enables the inclusion of more programming languages in the code
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit.  What is the action of the Bash script that is shown?
What is the action of the Bash script that is shown?
A) For all directories in the current folder, the script goes into the directory and makes a new directory.
B) The script waits until input is entered. If the directory exists, the script goes into it until there is no directory with the same name, then it creates a new directory.
C) The script waits until input is entered, then it goes into the directory entered and creates a new directory with the same name.
D) The script goes into the directory called "$ndir" and makes a new directory called "$ndir".
F) A) and D)
Correct Answer

verified
B
Correct Answer
verified
Multiple Choice
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue?
A) A router along the path has the wrong time.
B) A router along the path is misrouting the packets in a wrong direction.
C) The server is too loaded and the connection could not be handled in time.
D) The server is too far away and the packets require too much time to reach it.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit.  What caused the error in this API request?
What caused the error in this API request?
A) The API resource does not support the POST operation.
B) The submitted JSON payload has a formatting issue.
C) The API resource does not support JSON format payloads.
D) The submitted JSON payload includes a field that is not supported by the API resource.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit.  A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
A) only outbound connections between 3000 and 5000 are possible
B) port 3000
C) any port between 3000 and 5000
D) port 5000
F) A) and C)
Correct Answer

verified
B
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 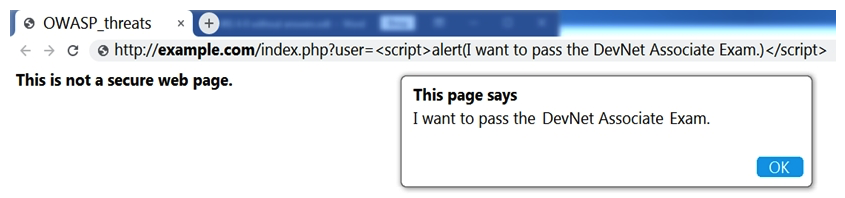 Which OWASP threat does this example demonstrate?
Which OWASP threat does this example demonstrate?
A) broken access control
B) cross-site scripting
C) SQL injection
D) man-in-the-middle
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 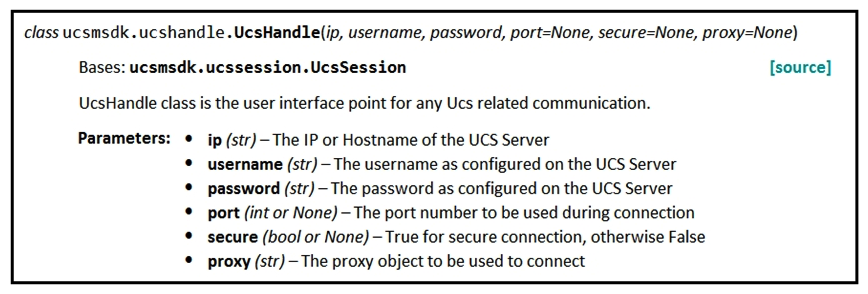 Given the API documentation for the UCS SDK Python class, Ucsl-landle, which code snippet creates a handle instance?
Given the API documentation for the UCS SDK Python class, Ucsl-landle, which code snippet creates a handle instance?
A) ![]()
B) ![]()
C) ![]()
D) ![]()
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two statements describe the advantages of using a version control system? (Choose two.)
A) It allows for branching and merging so that different tasks are worked on in isolation before they are merged into a feature or master branch.
B) It provides tooling to automate application builds and infrastructure provisioning.
C) It allows multiple engineers to work against the same code and configuration files and mange differences and conflicts.
D) It provides a system to track User Stories and allocate to backlogs.
E) It allows developers to write effective unit tests.
G) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the purpose of a MAC address on a network device?
A) unique network address that identifies the network interface of a device
B) unique network interlace address that is provided by the DHCP server
C) unique hardware address that identifies the network interface of a device
D) unique hardware interface address that is provided by the central switch
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. ![Refer to the exhibit. A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called vegetables . Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0]) A) {'color': 'green', 'items': ['kiwi', 'grape']} B) ['kiwi', 'grape'] C) lettuce D) kiwi](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_da9e_5cac_8515_55cb191da145_C1178_00.jpg) A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called "vegetables". Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])
A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called "vegetables". Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])
A) {'color': 'green', 'items': ['kiwi', 'grape']}
B) ['kiwi', 'grape']
C) lettuce
D) kiwi
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 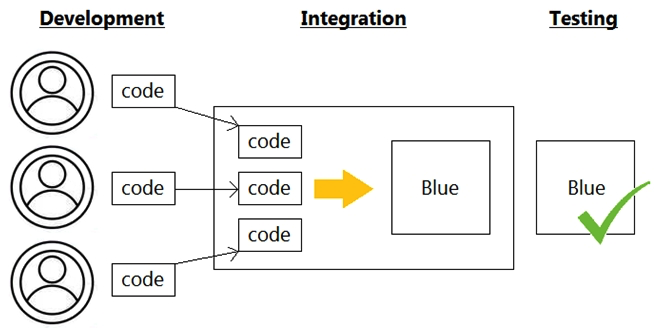 Which infrastructure automation method is shown?
Which infrastructure automation method is shown?
A) CI/CD pipeline
B) Lean
C) Agile
D) Waterfall
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are the purpose of the Cisco VIRL software tool?
A) to verify configurations against compliance standards
B) to automate API workflows
C) to simulate and model networks
D) to test performance of an application
F) All of the above
Correct Answer

verified
Correct Answer
verified
Showing 1 - 20 of 134
Related Exams